At Xcellerate, we help businesses boost their security posture with ThreatLocker®, a leading Zero Trust application allowlisting and storage control platform. Whether you face NIS2, DORA, or GDPR obligations, ThreatLocker® gives your IT department visibility, control, and compliance confidence.
Why ThreatLocker®?
- Zero trust by design – Deny all software by default, approve only known good business applications.
- Regulatory alignment – Enforce controls aligned with NIS2, DORA, GDPR.
- Full endpoint oversight – Block ransomware, unauthorized software, and unapproved storage.
- Audit-ready reporting – Instant proof of controls for compliance audits.
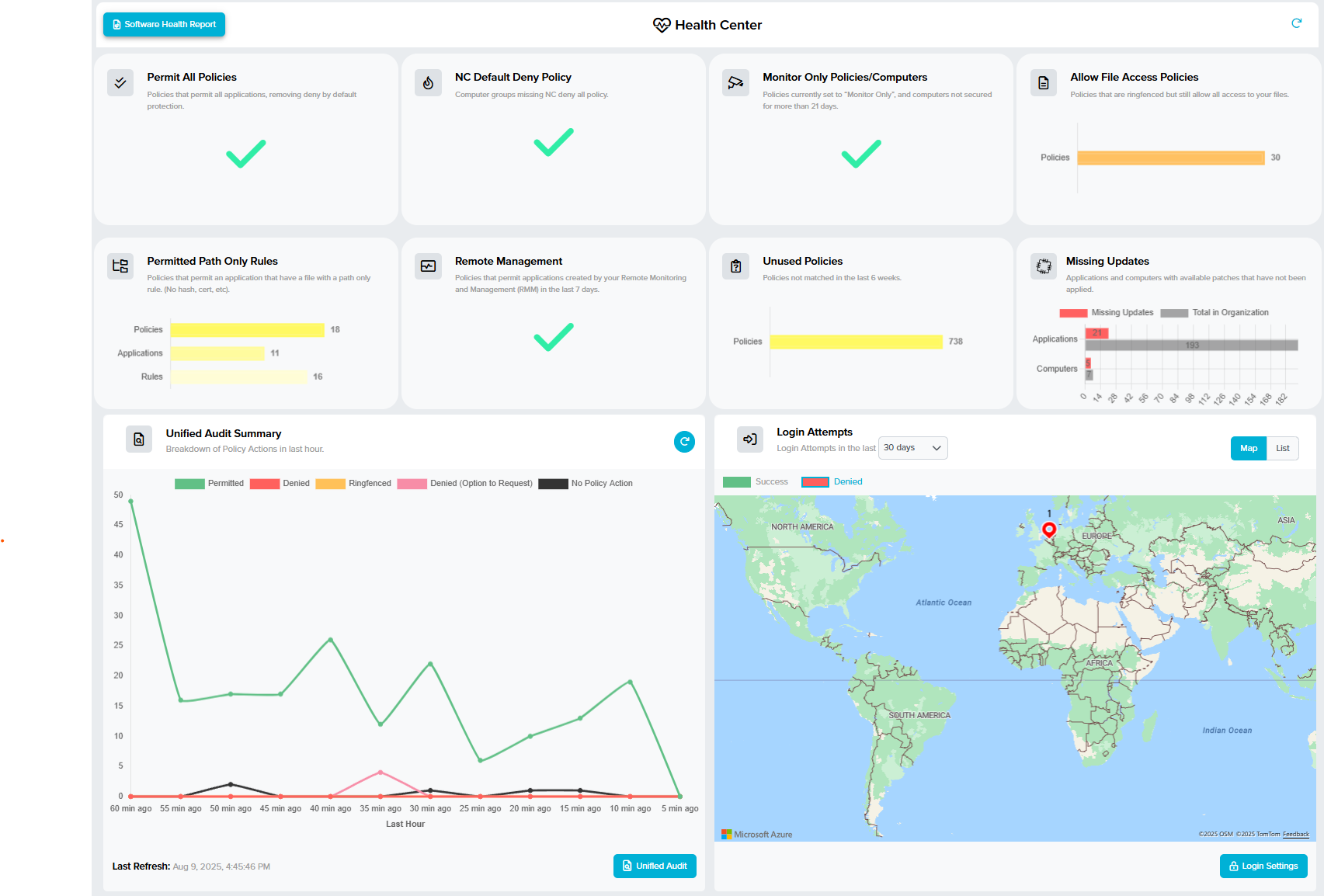
Figure 1: ThreatLocker dashboard – real-time monitoring of endpoints, policies, and compliance readiness.
What is Application Whitelisting?
While antivirus software is reactive and can fall behind the latest malware and ransomware variants, ThreatLocker’s whitelisting feature takes the opposite and proactive approach. It blocks all unapproved applications from executing by default, preventing cyber threats before they start. Legitimate applications can be easily approved, giving you complete control over what runs on your endpoints and servers.
- Default deny No applications run on your device unless you allow it.
- Learning mode picks up on the latest software updates where and when you choose.
- Approval New applications can be approved in minutes.
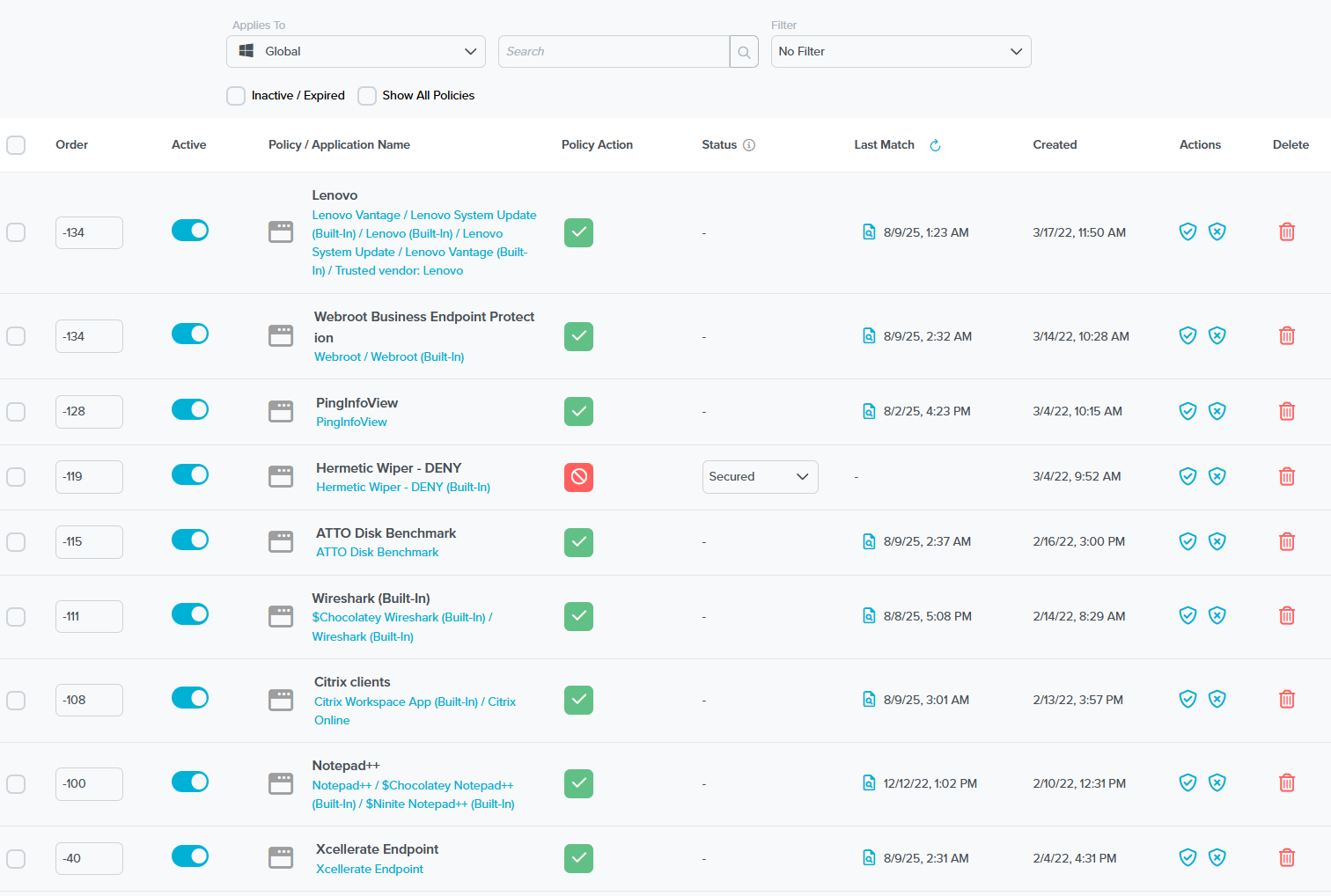
Figure 2: Build and enforce granular allowlist policies with ThreatLocker’s Policy Manager.
What is Storage Control?
Storage Control allows you to set up detailed rules on how storage devices can be used. Allow or block read/write/execute, limit what extensions, limit what software can use storage devices. Granular control and detailed auditing of every transaction that occurs on storage devices.
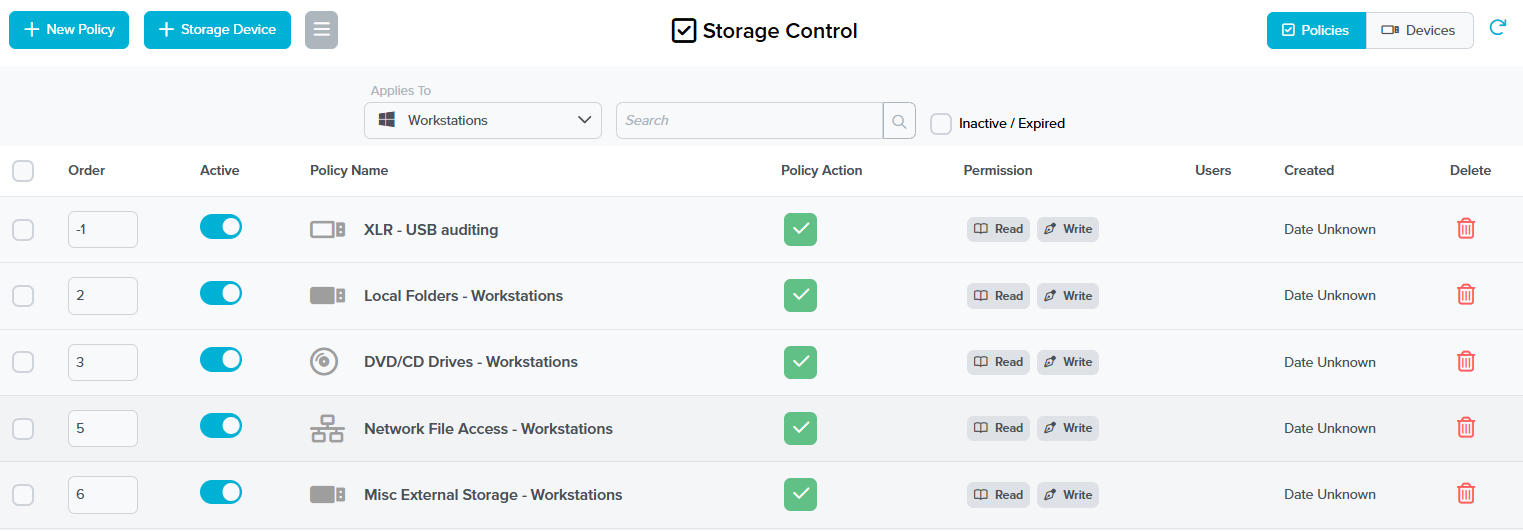
Figure 3: Storage control policies within ThreatLocker – block untrusted removable media while keeping business flow.
Get started with Xcellerate & ThreatLocker®
- Reduce ransomware exposure to a minimum.
- Maintain ongoing compliance posture.
- Respond swiftly to emerging threats.
- Streamline reporting for executives & regulators.
- Lower operational risk and complexity.
Your security shouldn’t wait for the next compliance deadline.
With ThreatLocker® deployed by Xcellerate, you secure every endpoint, enforce Zero Trust, and satisfy NIS2, DORA, and GDPR requirements – all with one platform.